Beware of Gift Card Scams
Garden State Cyber Threat Highlight
Original Release Date: 12/6/2023
Summary
It is commonplace for consumers to purchase gift cards as a present, especially for special occasions or the holidays. Threat actors seek to exploit this common task in gift card scams. For example, threat actors initiate fraudulent requests typically by spoofing a known or trusted person—such as a person in leadership or a position of authority within an organization, a friend, or a loved one—to make the request appear more legitimate. They also create a sense of urgency with a fake story or emergency to convince the recipient to act quickly without verifying. The fraudulent requests may be sent through email, SMS text messages, and social media platforms.
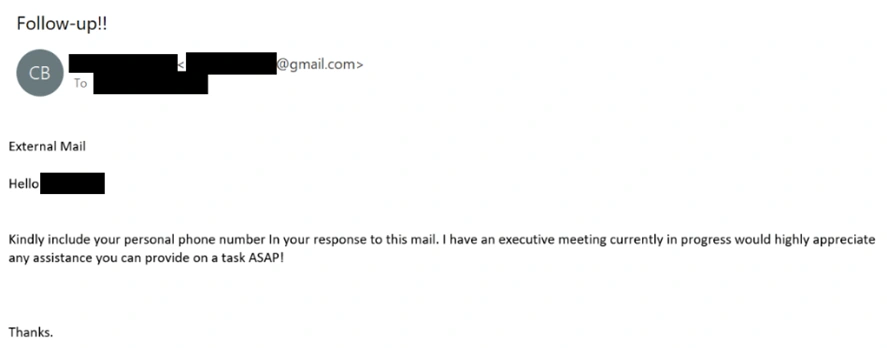
The NJCCIC continues to receive reports of gift card scams from New Jersey citizens and organizations. For example, an employee received an email sent from an external account purportedly from the CEO, who was attending a meeting out of state. The CEO requested their phone number to perform a task. The employee provided their phone number and then communicated through SMS text messages. The request was to purchase two $500 Apple gift cards, to which the victim complied and submitted the back of the gift cards. The request was identified as a scam when the victim was asked for the remaining balances.
The NJCCIC also continues to observe multiple campaigns identified as gift card scams attempting to convince New Jersey State employees to purchase gift cards to extort funds. The emails are primarily from free email providers instead of corporate domains. Threat actors may spoof the sender’s display name, which may differ from the sender’s email address in the header information. Additionally, they may contain a reply-to address that is different than the sender’s email address. Subject lines contain keywords such as “just touching base,” “favor,” “check in,” and “check up,” and the fraudulent requests typically begin with a brief message inquiring if the potential victim is available.
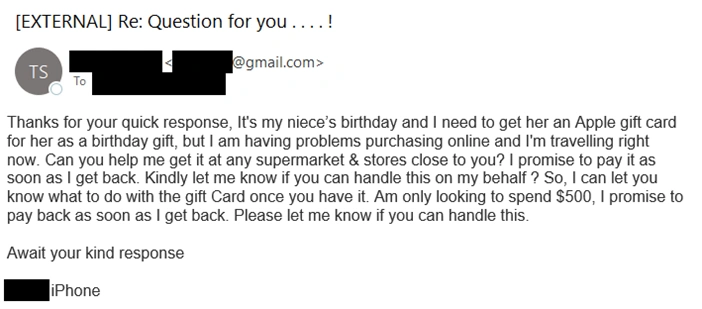
In the above campaign, threat actors state they are traveling and having an issue purchasing a $500 Apple gift card for their niece’s birthday. They request the recipient to purchase the gift card and will pay them back as soon as they get back. Other campaigns may, for example, apologize for bothering the potential victim and inquire if they have an Amazon account or order from them.
If the intended target replies or complies with the fraudulent request, the threat actors convince them to submit the gift card number and PIN found on the back of the cards. If submitted, the threat actors can use the gift card’s funds without the physical card since the funds are not linked to a specific person or entity. Additionally, victims typically will not be able to recover the funds used for purchasing the gift cards – even if the purchase was made by credit card – because the victim initiated the transaction, resulting in significant monetary losses.
Image Source: CBC
Other gift card scams include a card draining technique that tampers with physical gift cards on the display racks in retail stores. Threat actors may record the activation code on the gift card and put it back on the rack or adhere a fake barcode sticker over the real barcode. This technique permits them to secretly track when the gift card has been activated and load the funds onto their own gift card account immediately once the gift card is purchased. Therefore, when the purchaser or the recipient of the gift card attempts to use it, the gift card will be empty or invalid. Threat actors may also convince potential victims to buy gift cards at a discounted price on online platforms, such as websites, apps, or social media groups. However, if purchased, the threat actors will either send a fake or empty gift card or steal the gift card information and money without sending anything in return. Additionally, threat actors pose as trusted brands, such as Target, T-Mobile, Airbnb, United Airlines, Walmart, and Costco, and send emails or SMS text messages claiming the target will receive free gift cards or other rewards. To claim the rewards, these messages contain phishing links that, if clicked, direct the target to a fake survey website to steal personally identifiable information (PII) and financial information.
Recommendations
The NJCCIC recommends users and organizations educate themselves and others on these continuing threats and tactics to reduce victimization. Users are advised to refrain from responding to unsolicited communications, clicking links or opening attachments from unknown senders, and exercise caution with communications from known senders. If unsure of the legitimacy, contact the sender via a separate means of communication, such as by phone, before taking action. We remind users to refrain from complying with requests to purchase gift cards and sending the numbers to someone without first verifying the request via a separate means of communication. These are unusual requests or demands, typically portraying a sense of urgency, and should be handled with increased suspicion. If gift card information is sent, immediately contact the company who issued the gift card to inquire if the funds are still on the gift card and can be frozen. If PII has been compromised, review the Identity Theft and Compromised PII NJCCIC Informational Report for additional recommendations and resources, including credit freezes and enabling MFA on accounts.
Additionally, we recommend that consumers protect gift card purchases from potential fraud, treat gift cards like cash, and deal with only reputable and established companies or vendors. Also, inspect gift cards and their packaging before purchasing them to ensure no protective stickers or scratch-off codes have been tampered with. Consumers are also advised to check the activation receipt, check the balance frequently before the expiration date if gift card usage is delayed, and call the gift card’s customer service immediately for any suspicious activity or fraud, as some company’s rules have up to 60 days to report any fraud.
We encourage users to report cyber incidents via the NJCCIC Cyber Incident Report Form, the FTC Complaint website, and the FBI’s IC3 website. Additionally, users who send unsolicited emails or messages through online platforms may violate account policies and terms of use and should be reported to the sender’s email provider or associated online platform. Additional information can be found in the FTC resource.