Volt Typhoon
NJCCIC Alert
Original Release Date: 11/1/2023
Critical infrastructure organizations are urgently advised to identify signs of compromise on their systems and network that could be attributed to Volt Typhoon, a Chinese State-sponsored hacking group. Microsoft researchers have noted behavior that suggests the threat actors intend to conduct cyberespionage campaigns and maintain footholds within networks while avoiding detection. Furthermore, researchers assessed that Volt Typhoon is developing capabilities to disrupt critical infrastructure during future crises. In addition to the communications and transportation sectors, water and wastewater, energy, military and defense, and maritime sectors are perceived to be at risk.
In May, it was discovered that military networks on Guam and critical infrastructure networks in the United States had been targeted in attacks that Microsoft attributed to an emerging advanced persistent threat (APT) group dubbed Volt Typhoon. In July, the federal government confirmed that Volt Typhoon’s activity is more widespread than initially perceived, and CISA issued strong warnings that the public and private sectors must prepare and increase their efforts to secure networks.
Volt Typhoon targets critical infrastructure, and affected organizations include those in the communications, transportation, maritime, government, and education sectors and several others. They rely primarily on living off-the-land (LOTL) techniques and command line prompts, using internet-facing Fortinet FortiGuard devices as entry points and then routing traffic through other compromised small office and home office (SOHO) equipment to blend into normal network activity. They gain initial access by exploiting vulnerabilities for which patches exist, including CVE-2022-40684.
Their post-compromise activities include data exfiltration and credential compromise. Once they have obtained access, they issue commands to collect data, including credentials from local and network systems, store the data in an archive file to stage it for exfiltration, and then use the stolen credentials to maintain persistence.
Additional behavior includes discovering system information, including file system types, drive names, size, and free space, running processes, and open networks. They also attempt to discover other systems on the compromised network using PowerShell, Windows Management Instrumentation Command-line (WMIC), and the ping command. In a small number of cases, the threat actors run system checks to determine if they are operating within a virtualized environment.
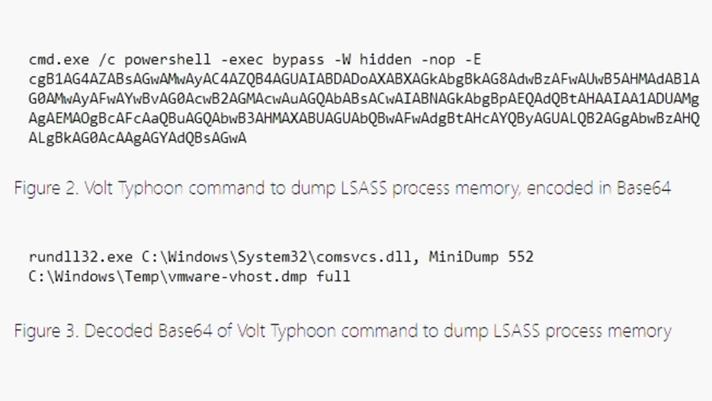
Microsoft has observed Volt Typhoon attempting to dump credentials using the Local Security Authority Subsystem Service (LSASS), which is demonstrated in Figure A.
Figure A: The top represents the encoded command prompt, and the decoded command is below. Source: Microsoft.
The NJCCIC advises organizations to patch vulnerable systems against known vulnerabilities, particularly those found in Fortinet FortiGuard devices, employ a defense-in-depth cybersecurity strategy, and monitor networks for suspicious activity using behavioral analysis. Follow cybersecurity best practices, harden the LSASS process, and run and monitor endpoint detection and response. Detection queries and artifacts associated with Volt Typhoon, including additional command prompts, indicators, and recommendations, can be reviewed in Microsoft’s analysis.