Don't Take the Bait! Phishing and Other Social Engineering Attacks
Informational Report
Original Release Date: 6/4/2018
Phishing is a type of social engineering attack that uses email, phone, social media, and other means of personal communication to trick individuals into providing sensitive information. This may include Personally Identifiable Information (PII), financial information, or login credentials. The attacker can use the information to gain access to online accounts, personal data, or other details for malicious attacks against individuals or organizations. Other phishing schemes intend to deliver malware to the end user system, often by opening malicious attachments or visiting malicious websites. The following are common types of phishing attacks and ways to identify them:
- Email Phishing is the most common type of phishing attack. The attacker sends emails pretending to be a legitimate entity, with the email containing links or attachments. Those links traditionally go to malicious websites that steal credentials or install malicious code. The attachments have malicious content stored in them that will install itself once the user opens the document. The attackers usually enact a sense of urgency within the email message to scare the user into doing what they want: to get the user to open the emails.
-
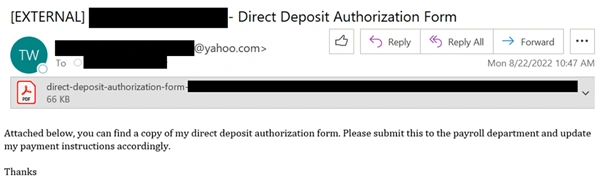
Business email compromise is one of the most common types of email phishing. The attacker sends an email from someone the target would trust, such as a colleague, boss, or vendor. The emails sender asks the recipient to take an action, such as logging into a fake website to obtain credentials, diverting payroll, transferring money, or purchasing gift cards.
-
- Spearphishing is similar to email phishing but with a personal touch. This phishing method involves gathering information specific to the target. Attackers customize their emails with the target’s name and any other personal information they could use to trick the recipient into believing the email was genuine.
- Whaling targets high-ranking members of an organization by crafting a personalized email that appears to be from a legitimate source. This type of attack requires research about the individual targeted. Then, the attacker uses the details they've gathered to craft a sophisticated email that will grab the target’s attention. The goal is to get the business executive or manager to reveal sensitive information, install malware, or transfer funds.
- Vishing is a phone-based form of phishing that takes place over the phone. The scammer calls claiming to be a trustworthy entity, attempting to convince the target to divulge sensitive personal information. A typical example is an attacker disguising themselves as an organization’s help desk technician or an external technical specialist to gain access to your devices.
- SMiShing or SMS-phishing is conducted through SMS text messages. The attacker sends a text message containing a link to a website of interest, or a request for the target to perform a task or provide sensitive information. SMiShing attacks can also be used to install malware on the target's device.
Other Popular Social Engineering Attacks:
- Baiting is a social engineering attack with the goal of luring targets in by making false promises. Baiting can be found in the form of enticing ads for things like free music or movie downloads. These ads can lead the user to malicious websites that encourage users to download malware-infected applications or attempt to steal credentials that the attacker can use to gain unauthorized account access. Baiting can also be used in physical form, most commonly with malware-infected flash drives. The attacker leaves the flash drive in an area where victims are likely to see it, with the hope that it is inserted into a computer that can provide the attacker with system and network access
- Pretexting involves the attacker creating a believable scenario and sharing it to convince the target to disclose sensitive data. Attackers that use pretexting may pretend to be someone in a position of authority, like a tax official, or a person of interest, such as a talent agent or sweepstakes organizer. After explaining the reason for contacting the individual, the attacker asks the victims questions that require information about the target’s identity – such as Social Security numbers, personal addresses, phone numbers, bank records, and even security information related to their job. This information could be used to perform other attack scenarios, gain access to the target’s personal accounts, or commit identity theft.
- Scareware relies on using fear and intimidation, overwhelming the target with false alarms and fake threats. The attackers convince the targets that their systems are infected with malware, which could come in the form of pop-ups that say there is a virus on the system. The attacker will create fraudulent websites asking for account credentials and, if submitted, the attacker will attempt to gain access to additional online accounts using the same credentials. The attacker can also distribute scareware through emails presented as illegitimate warnings, and may attempt to convince victims to buy fraudulent services.
Image 1: Sample Direct Deposit Business Email Compromise Phishing Email
How to detect a phishing email? Here are some questions to ask when a suspicious email is received.
- Does the email ask for sensitive information? Legitimate businesses will not request sensitive information (credit card information, social security number, and passwords) by email. If you receive an unsolicited email asking for any personal information, it may be a scam.
- Is the sender address and domain legitimate? Organizations have designated domains used to send emails. Inspect sender information to ensure the email address corresponds to the entity the email claims to come from. Threat actors will often use lookalike domains to appear legitimate.
- Does this email contain links that do not match the sending domain? Ensure links included in the email correspond to the email sender. Additionally, links requesting login credentials should be on official websites that are associated with the online service.
- Is the email personalized? Emails from legitimate entities often personalize their communications to their customers by using the recipient's name. Overly generic email messages can be a red flag that it is part of a broader phishing campaign.
- Is there poor spelling or grammar in this email? Legitimate businesses will have copywriters or editors review their communications.One of the easiest way to recognize a scam email is by looking at the grammar and spelling.
- Are there phrases or tactics often used to convince recipients into opening links or attachments? Many phishing schemes will attempt to trick or panic the recipient with an urgent and time-sensitive call to action. The goal is to make the recipient feel as if need to act immediately. Some commonly used phrases and tactics are: “We’ve noticed some suspicious activity or log-in attempts,” “There’s a problem with your account or payment information,” “You must confirm some personal information,” and “You need to make a payment.”
If you spot or suspect any common phishing email signs, do not interact with the links or attachments. Call the sender organization or entity directly via the phone using official numbers to confirm the legitimacy of a suspicious message.
Recommendations
The NJCCIC strongly recommends never clicking on links or opening attachments delivered with unexpected or unsolicited emails, social media messages, or text messages. If you accidentally do click on a suspicious link or visit a phishing website, do not enter any personal information on the site and disconnect your device from the network as soon as possible. Use your antivirus software to run a full scan of your system. If this occurs on a work system, contact your IT help desk immediately so that the system or device can be evaluated and quarantined if necessary to prevent the potential spread of a malware infection. If you entered or divulged personal information, monitor your bank accounts, credit profile, and other online accounts for any irregularities or suspicious behavior. If you do business with a company mentioned in a suspicious email, call the business and forward the email to them to verify the legitimacy of the email. In addition, do not reply to spam emails as this only verifies to the sender that your email account is active. Instead, delete the email. Lastly, use up-to-date antivirus software and firewall protection to prevent and block phishing attacks, and enable multi-factor authentication (MFA) for all accounts that offer it to greatly reduce your risk of account compromise via credential theft. For organizations, one of the most effective ways to prevent incidents resulting from phishing attacks is through employee training and awareness.
SMiShing messages can be reported by forwarding the SMS text to 7726.
In addition to the NJCCIC, phishing messages can be reported to https://phish.report/.