Encryption: The Basics
Informational Report
Original Release Date: 8/29/2022
Imagine being back in grade school, and you are passing a paper note to a friend on the other side of the classroom. That note was only meant for your friend to see, as it has an embarrassing message on it. Now imagine how mortified you would feel if another student opened the note and read it, dooming you to your classmates' ridicule. This same framework can be applied to professional environments. If that note contained sensitive company data and an unauthorized party gained access to that information, they could potentially obtain employee data, intellectual property, or trade secrets and launch subsequent cyberattacks. Keeping unauthorized parties from viewing your sensitive data is where encryption comes into play. Without an associated decryption key, nefarious actors - or nosy classmates - will not be able to view sensitive information.
Encryption Through the Centuries
The concept of encryption was part of human civilization long before computers. One of the oldest ciphers recorded was known as the Caesar cipher, which was used by Julius Caesar to send private messages to avoid the prying eyes of his political enemies. The Caesar cipher is relatively simple, each letter in the unencrypted message (also known as plaintext) would be moved a fixed number of positions down the alphabet. For example, if during the encryption process the plaintext was shifted 5 positions to the right, any “a” in the message would become an “f”, any “b” would become a “g”, and so on. This substitution cipher would turn the plaintext into an encrypted message, also known as ciphertext. Another well-known cipher was the Enigma cipher, used by Germany during World War II. The Enigma cipher worked on a physical machine, which contained a series of rotors that encrypted the plaintext message typed into the machine and transmitted it to another machine that would decrypt it. Every machine’s encryption setting was changed daily, making this encryption method hard to decipher. The Enigma cipher was eventually cracked thanks to Polish cryptanalysts and enhanced by Alan Turing’s bombe machine, which was able to calculate the encryption changes more accurately and help the Allies intercept German encrypted messages. While these ciphers were formidable during the time of their creation, modern day computers can crack these antiquated ciphers with ease.
How Encryption Works
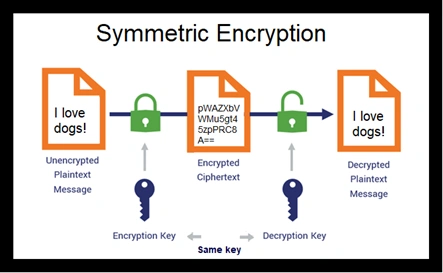
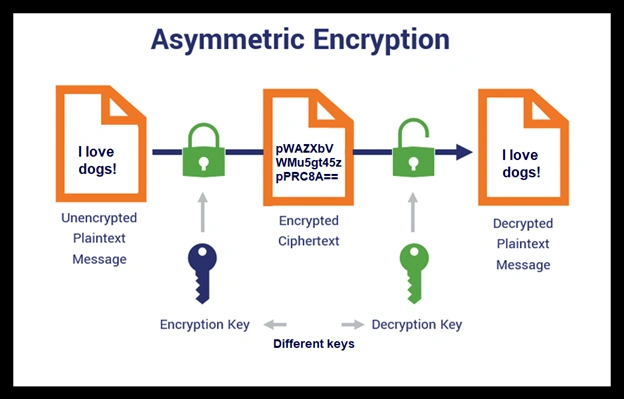
Even though we might not realize it, we rely on encryption in our daily lives. From the information submitted on a website to the data on your device, encryption is used in many ways. Encryption works through the use of cryptographic keys, which change the data into an incomprehensible block of data. Just like a physical lock, this block of encrypted data can only be “unlocked” by a key that is either owned by the recipient of the message or authorized by the sender. The nature of cryptographic keys varies depending on the type of encryption use. Two main types of encryption are symmetric (single key) encryption and asymmetric (public key) encryption.
Symmetric Encryption vs Asymmetric Encryption: What’s the Difference?
Both symmetric and asymmetric encryption use cryptographic keys to secure data, but how they encrypt and decrypt data and the types of data they are meant to encrypt vary.
Symmetric encryption is an older, simpler, and faster method compared to asymmetric encryption. Symmetric encryption uses the same key to both encrypt and decrypt data. This saves time, but is also less secure than asymmetric encryption. One of the main uses of symmetric encryption is for securing websites. When browsing a website preceded with HTTPS, the connection to that website is secured with Transport Layer Security (TLS), a form of symmetric encryption. This method is also often used to secure data at rest, as symmetric encryption can encrypt a large amount of data at once. Currently, the most secure form of symmetric encryption is the Advanced Encryption Standard (AES), which uses 128, 192, or 256-bit keys to encrypt data blocks of 128 bits.
Asymmetric encryption, though slower and more resource intensive than symmetric encryption, is far more secure as it uses two separate keys to encrypt and decrypt data. For this reason, asymmetric encryption is often used for more sensitive data in which the speed of encryption is not a primary concern. Asymmetric encryption can be used to transmit small amounts of sensitive data, such as when using digital signatures, authorizing cryptocurrency transactions on the blockchain, and when transporting other cryptographic keys to an intended user, such as during a TLS handshake. For the latter example, asymmetric and symmetric encryption is used together to secure your web browsing experience. In asymmetric encryption, the sender uses a public key to encrypt data and then it is transported to a receiver, where a private key is used to decrypt the data. This method of encryption is more secure than symmetric encryption; if a threat actor obtained the sender’s public key, they would still be unable to decrypt the data without the recipient's private key.
The Weaponization of Encryption
As with many cybersecurity tools used by network defenders, cyber threat actors can find ways to weaponize these tools for their own nefarious means, including in ransomware attacks. In these incidents, threat actors encrypt resources on the network (including files, and other data), preventing access to the resources unless a ransom is paid to receive the decryption key. Ransomware, like many other forms of malware, can be spread through malicious emails, unauthorized access, malware, and more. Once ransomware infects a system, it encrypts the contents of that system and potentially spreads to other parts of the network to encrypt accessible systems and resources. The threat actor will typically ask the victim for a large sum of money in exchange for the cryptographic key that is used to decrypt the data encrypted. Ransomware is a significant threat, as it is time-consuming and costly to recover from these cyberattacks, regardless of whether a ransom is paid. For proactive recommendations to become more resilient to ransomware attacks, please see the Ransomware: Risk Mitigation Strategies NJCCIC guide.