The Threat of Social Engineering
Garden State Cyber Threat Highlight
Original Release Date: 8/5/2021
Threat actors use various tactics and techniques in social engineering scams to impersonate known organizations and individuals, employ the use of urgency or authority, steal user credentials and other sensitive information, and deliver malware. The NJCCIC continues to observe and receive reports of social engineering scams, including phishing, Business Email Compromise (BEC) scams, vishing, and SMiShing. We provide examples and recommendations to educate users and organizations and reduce the likelihood of victimization.
Social Engineering Scams
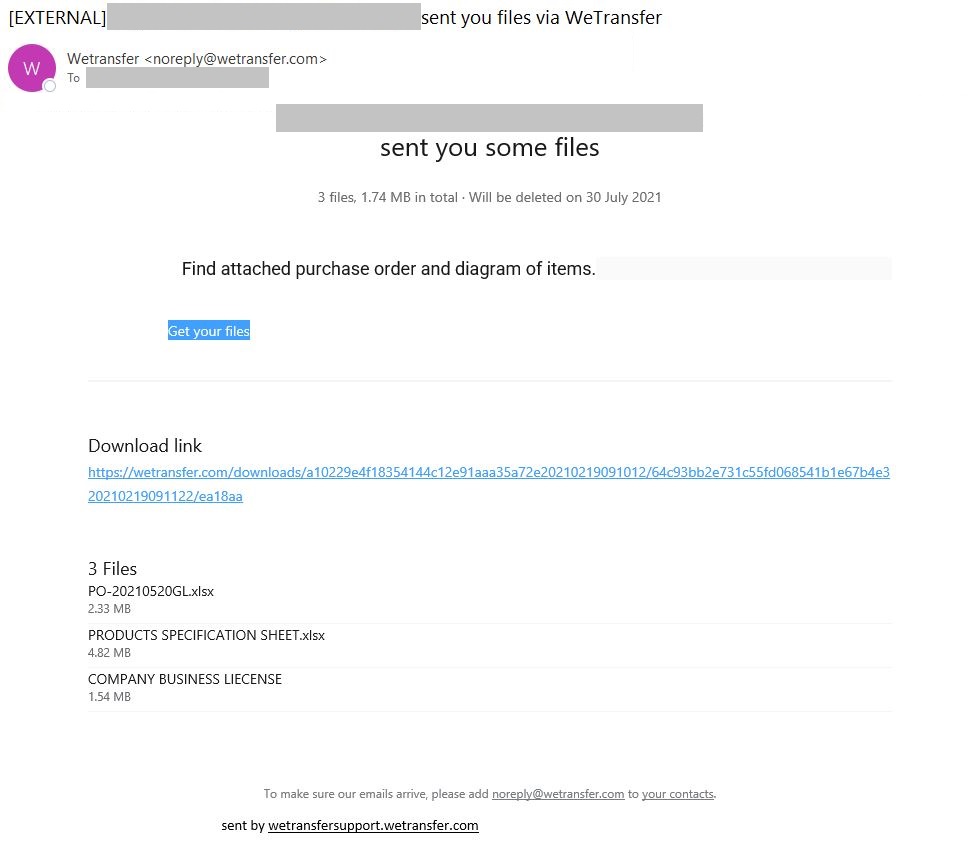
The NJCCIC continues to observe multiple phishing campaigns attempting to be delivered to New Jersey state employees to steal credentials and deliver malware. Threat actors target file-sharing websites since they are commonly used for business purposes and may provide access to sensitive information. A recent phishing campaign purports to be from WeTransfer, an internet-based computer file transfer service. In the example below, the phishing email spoofs a WeTransfer file-sharing notification and convinces the user to retrieve the files by clicking on the link. If clicked, the user is redirected to a Discordapp URL to download a compressed executable that installs a remote access trojan (RAT).
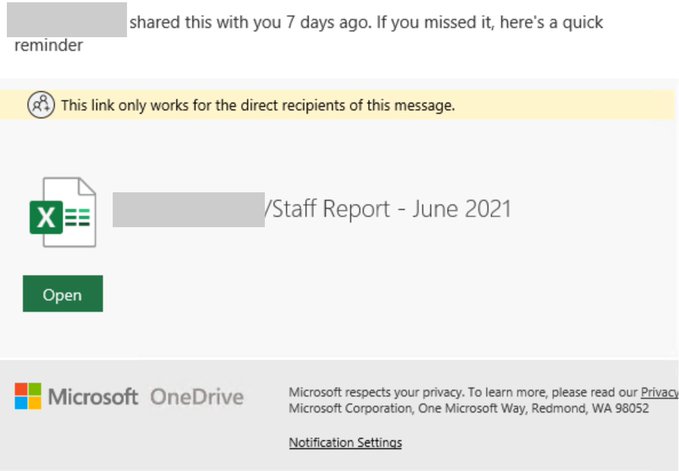
A similar phishing campaign in open-source reporting also spoofed WeTransfer, claimed the victim was sent several files, and contained a link to view these files. If clicked, the link led to a phishing webpage with Microsoft Excel branding to appear to look like a legitimate Microsoft login webpage and displayed the victim’s email address already populated in the form. This campaign was intended to steal victims’ O365 account credentials. The targeting of O365 account credentials is not new and continues to be a prime target for threat actors, as 43 percent of all phishing attacks involve the impersonation of Microsoft brands. Microsoft recently warned of a phishing campaign using a SharePoint lure purporting to be a file share request to access enticing information—such as “staff reports,” “bonuses,” and “pricebooks”—and then direct the user to a phishing page to steal credentials.
Threat actors will use various lures and platforms to try to bypass phishing protections. Microsoft recently introduced phishing protections against malicious link-based phishing attacks called Safe Links in Microsoft Defender for Office 365, which checks URLs before the page is opened.
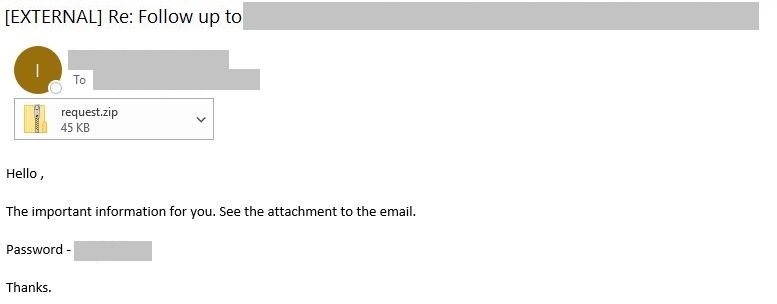
Several months ago, the NJCCIC reported on threat actors targeting Office 365/Microsoft 365 customers using phishing tactics and call centers to trick targets into downloading Baza(r)Loader malware, dubbed “Baza(r)Call.” The NJCCIC continues to observe phishing emails attempted to be delivered to New Jersey state employees to download BazaLoader. The phishing emails appear to be replies to older conversation threads and contain password-protected zipped Microsoft Word attachments. If macros are enabled, the BazaLoader malware is downloaded and installed as a backdoor.
Microsoft warned that the BazaCall operation is more dangerous than originally discussed, with capabilities to move quickly within a network, conduct data exfiltration and credential theft, and distribute ransomware, such as Ryuk or Conti, within 48 hours of initial compromise.
The NJCCIC also continues to receive reports of social engineering scams from NJ businesses, agencies, and individuals. Multiple staff members within an organization reported that they received emails from themselves claiming there were hacked and advised to pay in bitcoin. It is believed the email addresses were spoofed and the emails were similar in nature to previously reported sextortion scams. In addition to the NJCCIC, phishing emails can be reported to https://phish.report/.
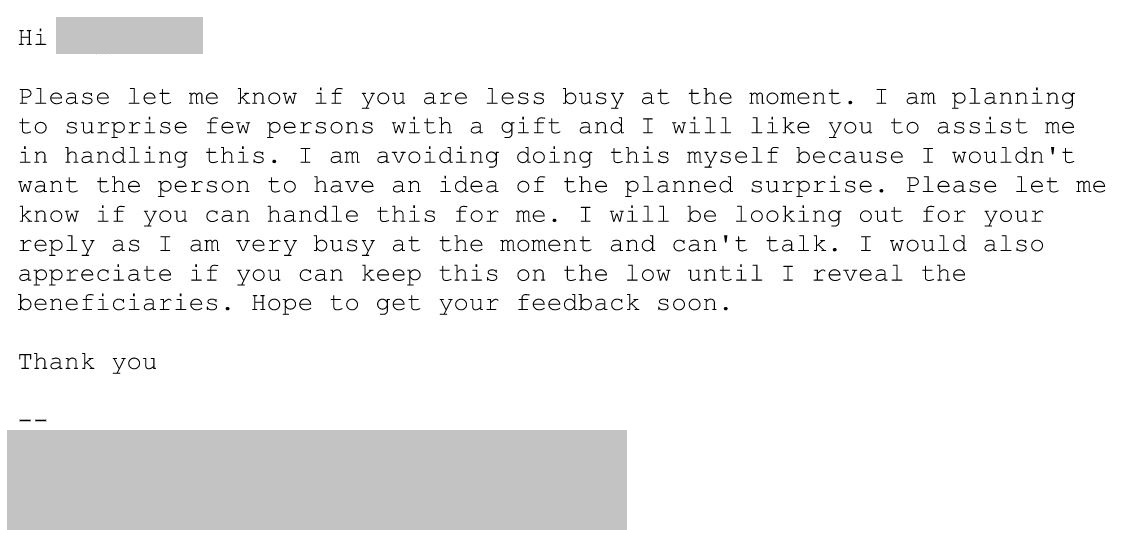
The Business Email Compromise (BEC) scam below was sent individually from a Gmail account purporting to be from a senior level executive position in an attempt to convince their employees to perform a task or reveal sensitive information. The body of the email was addressed with the recipient’s first name and signed using the full name and credentials of the impersonated executive.
Social engineering scams are also conducted via phone calls and SMS text messages. A caller claiming to be from Medicare with a caller ID of a NJ area code advised the target of a new Medicare card replacement for their current card and requested the Medicare number on the old card. When the target did not provide that information, the caller claimed they made a mistake with the target’s information and requested their Social Security number (SSN) instead. The caller also inquired if other members in the household had a Medicare card or SSN card. To report SMiShing messages, forward the SMS text to 7726.
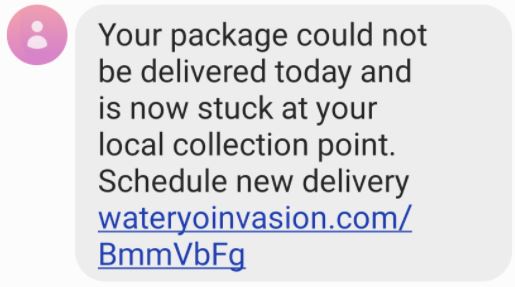
In the SMiShing example below, the message creates a sense of urgency by claiming there is an issue delivering a package and convincing the user to schedule a new delivery by clicking on the link. If the link is clicked, the victim is directed to a suspicious website instead of an authentic shipping or vendor website.
Recommendations
Organizations can employ the following defensive measures to create a more cyber resilient environment to reduce the risk of social engineering attacks:
- Security awareness training. Train employees to help better understand cyber threats and provide a strong line of defense.
- Use unique, complex passwords for all devices/accounts. Unique passwords for each device/account prevents password reuse attacks, in which threat actors obtain your password for one account and use it to compromise an additional account using the same credentials.
- Enable multi-factor authentication (MFA) where available: MFA is the use of two or more factors to authenticate to an account or service. This significantly reduces the risk of account compromise via credential theft in which your password has been exposed. Although MFA is an additional step to authenticate, it is an important one—not only to protect an individual account, but also the community at large.
- Exercise caution with communications. Refrain from divulging sensitive information via phone, text messaging, or email without verifying the requestor via a separate means of communication before taking any action.
- Refrain from sharing or saving login credentials or other sensitive information. Login credentials and other sensitive information should not be shared with anyone. Avoid auto-saving passwords, payment card numbers, or contact information when prompted by your operating system, browser, website, or applications.
- Navigate directly to websites. Navigate directly to authentic or official websites by typing the legitimate URL into the browser instead of clicking on links in messages, and refrain from entering login credentials on websites visited via links delivered in messages.
- Use secure websites. When sharing personal or financial information, ensure you are using verified, secure, and encrypted websites.
- Secure physical devices. Safeguard devices and ensure a password/passcode is enabled for all devices to prevent unauthorized access.
- Keep devices up to date. Stay informed about publicly-disclosed vulnerabilities and update devices—including firmware—to the latest version to ensure they are patched against known vulnerabilities that could be exploited by threat actors to gain unauthorized access to your device and/or data. If a device is unable to receive updates from the vendor, consider not purchasing or discontinuing use of the device.
- Incident reporting. Report malicious cyber activity to the NJCCIC via the Cyber Incident Report form and/or report data breaches to the NJCCIC via the Data Breach Report form.