Data Breach Prevention, Response, and Resources
Informational Report
Original Release Date: 6/16/2021
Threat actors target valuable data, such as personally identifiable information (PII), protected health information (PHI), criminal justice information, student educational records, intellectual property, and financial and payment card information. If valuable data is insecure and accessible, it is a matter of when, not if, it is located and exposed. Cyber incidents continue to increase and, as a result, data breaches are unfortunately becoming the norm. Not all cyber incidents result in data breaches; however, all data breaches are a result of cyber incidents. In an effort to reduce the likelihood and impact of cyber incidents and prevent data breaches, it is important for organizations to prepare for and respond efficiently and effectively to cyber incidents, collaborate with law enforcement and intelligence agencies, report data breaches, and implement cybersecurity best practices.
Incident Response
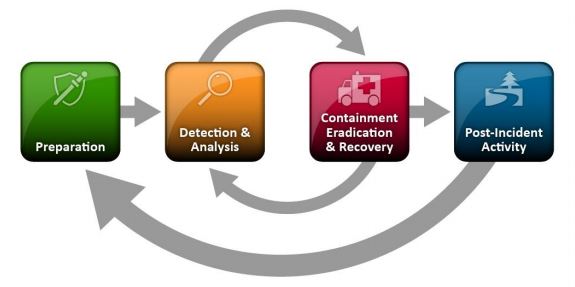
Incident response is critical in the event of a cyber incident. The National Institute of Standards and Technology (NIST) sets standards and practices for cybersecurity and responding efficiently and effectively to incidents as outlined in the four main phases of the NIST Incident Response Life Cycle:
- Preparation: This initial phase involves establishing and training an incident response team and acquiring the necessary tools and resources. Preparation is the key to effective and rapid response to help limit the impact of cyber incidents. This phase includes compiling a list of all assets, creating a communication plan (describing who to contact and what to do), and creating an incident response plan. Controls should also be selected and implemented based on the results of risk assessments; however, residual risk will inevitably persist after controls are implemented. This phase should also include defining security events and their thresholds to be investigated.
- Detection and Analysis: Detection is necessary to alert organizations whenever there are indications of a potential security incident. Accurately detecting and assessing incidents is often the most difficult part of incident response for many organizations.
- Containment, Eradication, and Recovery: This phase includes patching the threat’s entry point, removing the threat, and ensuring systems are operational or back to business as usual. In keeping with the severity of the incident, the organization can mitigate the impact of the incident by containing it and ultimately recovering from it. This phase also focuses on keeping the incident impact as minimal as possible and mitigating service disruptions. Activity may cycle back to the previous phase to see if additional incidents are detected while eradicating the initial incident.
- Post-Incident Activity: After the incident is adequately handled and operations are back to normal, a review of the incident is just as important as the preparation. This phase includes conducting a root cause analysis of the incident and analyzing incident response efforts. It is important to understand why the incident happened, its impact, what actions were taken to mitigate it and resolve it, and what should be done to prevent or better respond to future incidents. Learning from the experience, identifying areas for improvement, and updating the documentation are some of the most important, yet most often ignored, parts of incident response.
NIST Incident Response Life Cycle
Image Source: NIST
The incident response plan should be implemented, rehearsed, and tested regularly with critical stakeholders so that relevant parties are aware of their responsibilities and can respond properly to minimize downtime and cost to the organization in the event of a cyber incident. Tabletop exercises are highly recommended to identify valuable data and critical assets, account for roles and responsibilities, review various scenarios, assess risk, and adjust any procedures and guidelines as necessary. Lastly, the incident response plan should be complete, sufficiently detailed, and current.
Cyber Insurance
Cyber insurance has quickly become an essential resource for businesses. While having some form of cyber insurance in place can help an organization in the event of a cyber incident, an organization is also responsible for its own cybersecurity and the responsibility is not shifted to the insurer. Cyber insurance has emerged as a standalone line of coverage that can help mitigate losses from a variety of cyber incidents and its aftermath, including data breaches, business interruptions, and network damage. Large organizations may have coverage to transfer risk and costs associated with a data breach, whereas smaller organizations may not.
The cost of a cyber insurance policy will depend on a number of different factors including the size of the organization, annual revenue, the industry in which it operates, the sensitivity of data handled, and the overall security of the network. For example, underwriting data recovery and system forensics would help cover some of the cost of investigating and remediating a cyber incident by employing forensic cybersecurity professionals to aid in discovering attack vectors and remediation of vulnerabilities. In the case of ransomware, some insurance companies also cover the cost of paying the ransom, despite guidance from law enforcement and the information security community. The insurance company looks at what the potential incident response and forensic bill might be. Unfortunately, this bill will be more costly in most cases as many organizations are not prepared and, therefore, insurance companies would rather pay the ransom.
Organizations will need to make sure they understand what is covered and, perhaps more importantly, what is not covered when agreeing to a coverage policy. Plans may not cover legal costs or penalties. There may also be an additional deductible not covered in the overall costs. Depending on several factors—such as disclosure requirements, the size of the breach, and other things hiding in the fine print—that damage can be considerable. Therefore, organizations should ensure they know exactly what their cyber insurance policy covers and understand the potential costs of the most likely cyber incidents, such as ransomware.
Collaborative Efforts with Law Enforcement and Intelligence Agencies
Reporting cyber incidents to law enforcement is becoming a common requirement for insurance companies, and is also beneficial to organizations by providing guidance and access to additional resources. In the event of a law enforcement cyber investigation, remediation of the incident will not be hindered nor will the organization be forced to halt their operations.
Cyber incidents can also be reported to intelligence agencies, such as the NJCCIC via the Cyber Incident Form, in an effort to bridge the information sharing gaps between local, state, federal, public, and private sector organizations to reduce cyber risk and respond to emergent incidents. Organizations may not be aware of specific threats, trends, suspicious indicators, or vulnerabilities. Organizations willing to provide incident details—such as attack vectors, vulnerabilities exploited, and tactics used—will assist others in increasing their resiliency to these various threats.
Mandatory Data Breach Reporting
Organizations have an obligation to protect information and report a breach of security. According to the New Jersey Identity Theft Prevention Act, a "breach of security" is defined as the “unauthorized access to electronic files, media or data containing personal information that compromises the security, confidentiality, or integrity of personal information when access to the personal information has not been secured by encryption or by any other method or technology that renders the personal information unreadable or unusable.” Furthermore, any organization that conducts business in New Jersey, or any public entity that compiles or maintains computerized records that include personal information, are required to disclose any breach of security of those records following discovery or notification of the breach to any New Jersey resident whose personal information was, or is reasonably believed to have been, accessed by an unauthorized person.
Organizations are mandated by law to report data breaches and the NJCCIC provides the reporting mechanism for data breaches via the State of New Jersey Data Breach Report Form. When filing a data breach report, organizations are required to provide data breach details, including the number of NJ residents affected, data compromised (including PII), and consumer notification. Once submitted, it is reported to the NJCCIC for intelligence purposes, the NJ State Police for possible criminal activity, and the NJ Office of Attorney General for consumer impact. For more information and questions on data breaches, the law, and reporting, please contact the NJ Office of the Attorney General, Office of Consumer Protection.
In the event of a data breach, organizations should communicate and report information in a timely, accurate, and transparent manner to impacted business partners, regulators, and/or consumers. After a breach is discovered, organizations typically issue a public statement and offer a free comprehensive package of identity theft protection and credit file monitoring. If it is suspected that personally identifiable information (PII) has been compromised, impacted consumers are advised to review the NJCCIC Informational Report Compromised PII: Facilitating Malicious Targeting and Fraudulent Activity for recommendations and resources, including information on credit freezes and enabling multi-factor authentication (MFA) on accounts.
Cybersecurity Best Practices
The NJCCIC provides individuals and organizations with information and resources for cybersecurity best practices and implementing preventive measures to help protect themselves from cyber incidents and data breaches. The NJ Statewide information Security Manual (SISM) includes a set of policies, standards, procedures, and guidelines. It sets a clear direction for information security, and it also provides effective management of risk and ensures the confidentiality, integrity, and availability of information and information systems. It has been derived from State and federal laws, industry best practices, and lessons learned, along with New Jersey State Government business and technology-related considerations. Additionally, the NJCCIC Cybersecurity Program Controls Assessment, which is aligned with the NJ SISM, covers many control areas and helps organizations understand their own cybersecurity program and identify risks and establish strategies and tactics to manage them. The Assessment can be obtained by emailing the NJCCIC at njccic@cyber.nj.gov.