User Beware: Your Smartphone Is Tracking Your Every Move
This Is Security
Original Release Date: 8/26/2020
Updated: 1/6/2023
Every breath you take and every move you make
Every bond you break, every step you take, I'll be watching you
Every single day and every word you say
Every game you play, every night you stay, I'll be watching you…
In 1983, when The Police released the hit song, “Every Breath You Take,” they likely had no idea its lyrics would so aptly describe how smartphones can be used today. From services to apps, smartphone users unwittingly consent to being tracked in real-time by a multitude of companies for the purpose of providing requested features, integrations, user experience improvements, and many other laudable-sounding reasons. What many users do not know is that detailed information on their precise location and activity is being beaconed out by their phone and collected, shared, and sold to numerous organizations that aggregate these data sources with others to build a user profile that would make spy agencies and repressive governments green with envy.
The necessity and utility of smartphones is unarguable today. This article is not intended to suggest that individuals discard them. Instead, its purpose is to provide some insight into the unintended privacy and security implications of using smartphones. In addition, the recommendations detailing steps to limit what personal information is shared are not meant to be comprehensive; they only provide some level of awareness and control. Unfortunately, you can implement all the suggested security and privacy controls listed below and still be tracked with full fidelity.
While this article is focused on smartphone data trails, all sorts of other devices, such as your vehicle’s entertainment system, your fitness tracking device, your smartwatch, and just about any other device that emanates a network signal – including cellular, Wi-Fi, Bluetooth, and near-field communications (NFC) – can be used to track your location and other identifying information. In the case of a smartphone, all these network signals could be compiled to essentially publish a diary of your daily activities for the world to read.
Below are some tips to mitigate smartphone security and privacy risks.
- Physical Security and Access: Smartphones are easy to lose and just as easy to steal, so it important to start with physical security. Make sure to keep your smartphone in sight or always secured and protect its contents by implementing a screen lock that requires a passcode, fingerprint, or face ID for access. If your unlocked device is stolen, the criminal has the keys to your kingdom.
- Beaconing Services: Upon powering on your phone, one of the first things it does is register itself with the nearest cellular tower. Since most people need the cellular network for voice and data communications, it may not be practical to turn off cellular access. Even if you did, your phone would still send out beacons if Wi-Fi or Bluetooth are enabled. To shut down beaconing services, consider enabling airplane/flight mode. You will still be able to play music and look at data already stored on your device, but you, and your device, will not be able to communicate wirelessly.
NFC is used for various payment services, such as Apple Pay on an iPhone. If you do not set up Apple Pay, then NFC will not be activated; however, there is no way to deactivate NFC on an Apple device if Apple Pay is set up. For Android phones, NFC can be disabled in the Settings -> Connected Devices -> Connection Preferences screen.
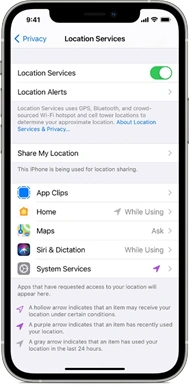
- Location Services: Mapping apps on your smartphone have all but eliminated the need for paper maps or stopping to ask a stranger for directions. Google Maps, Apple Maps, Waze, and other mapping apps use the GPS service on your phone to identify your location and provide directions to your destination of choice. It makes sense to enable location services for mapping apps, but there are numerous apps with no need to know your location that still request access. If your free flashlight application requires location services, then you must really be lost. Similarly, 2+2=4 regardless of where you are, so calculator apps do not need access to your GPS. Even weather apps do not need to use the GPS on your phone, as users simply need to type in the location of where they want to know the weather. Many of these apps, particularly the free ones, request excessive, unnecessary permissions to sell the data they collect from you, including your location data.
 |
 |
| Apple Location Settings | Android Location Settings |
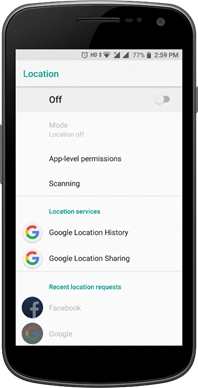
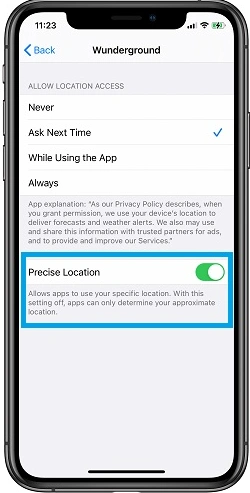
Apple and Google provide several options that allow users to control location settings and which apps have access to them. Smartphone owners are advised to review their phone’s location settings and only enable them as necessary for use by applications that you approve. Location Services settings for iPhone can be managed from the Settings -> Privacy & Security -> Location Services screen. For Android devices, swipe down on your screen and tap the location icon to configure your device’s location services. Users may also elect to prevent location services from identifying their precise location and instead choose a relative area, as shown in the below image.
 |
 |
Apple Precise Location Setting
|
Location Data Location data is important to advertising efforts of many businesses, including tech giant Google. The sensitivity of location data requires controls to protect organizations from abusing data collection and sharing. Though no specific federal law regulates the use, collection, or sharing of user location data, many organizations have implemented policies regarding privacy protection and most states have laws to protect consumer privacy and limit how consumers’ data may be used, stored, and shared. During an investigation by lead by several states, Google was found to be in violation of consumer protection laws, including New Jersey’s Consumer Fraud Act, by misleading users regarding location tracking. Google users who turned location settings to “off” could still be tracked using a separate setting, Web & App Activity, which is turned “on” by default when accounts are created. As a result of this violation, Google agreed to pay nearly $392 million to 40 states in what is reportedly the largest multistate privacy settlement. As part of the agreement, Google committed to increasing clarity on its location-tracking practices with users. These adjustments include showing users more information when they turn location tracking on or off and providing a details of the location data routinely collected on a webpage consumers access. With the increase in location data usage for advertising and increased mobile features for location privacy, taking extra steps to verify device settings will provide more control over what data is collected and when and how it can be used. |
- Apps: Prior to downloading and installing an app, conduct some research. If the app is storing sensitive data, is it encrypted in transit and at rest? Many app makers include privacy policies that are so obtuse and confounding that reading them provides no insight whatsoever into what they are doing with your data. At the very least, make sure they have a policy and try to obtain some more information on how they treat your data. Read reviews and search for complaints made against the company or about data beaches it may have suffered.
Once an app is installed, review the privacy settings on your phone to control what it can access. Does the app need to access your contacts, calendar, or photos? Configure privacy settings as appropriate. Apple and Google continue to implement privacy restrictions for apps they allow into their app stores and keep your apps up to date.
|
Paranoia or Real Threat TikTok is a very popular short-form video sharing and social networking app that is also at the center of ongoing security and privacy controversy since it is owned by the Chinese technology company, ByteDance. As a registered Chinese company, ByteDance is required to fully cooperate with the Chinese government. As such, there are national security concerns about user data the Chinese government might require ByteDance to provide. Analysis of various versions of TikTok have been found to collect the keystrokes of users, make screen captures every few seconds, access data from the phone’s clipboard, and collect the unique Media Access Control (MAC) address of the device, among other user information. That data may include your passwords and other sensitive information you enter or access – not only into the TikTok app, but also the other apps you use on your device, e.g., email, text messages, eHealth apps, etc. Due to these issues and ByteDance’s ties to the Chinese government, the US Department of Defense, various federal agencies, corporations, and governments around the world have banned TikTok from being installed on their devices. TikTok is not alone in collecting user data. Many apps do, and while those app makers may not provide that data directly to the Chinese government or other regimes that pose national security risks, those governments may ultimately obtain that data through intermediary companies and brokers. Users and organizations must be aware of these risks before installing apps on their phones. In August 2020, then-President Donald Trump issued an executive order requiring China's ByteDance to divest ownership of its US assets. In addition, ByteDance is required to destroy all its copies of TikTok data attached to US users and inform the Committee on Foreign Investment in the United States (CFIUS) when it has destroyed the data. ByteDance is challenging the order in court. |
- Software Development Kits (SDKs): There are millions of mobile apps in the Apple App Store and Google Play, and many of them use third-party code libraries, Application Program Interfaces (APIs), and SDKs to facilitate the creation of an app without having to write every line of code from scratch. SDKs allow app developers to easily add features and functionality to the apps they are developing. Yelp and Uber, for example, use SDKs from Google Maps to provide mapping functionality. Some apps will allow you to log in using your Facebook or Google credentials, functions made available by SDKs from Facebook and Google, respectively. Apple and Google also provide app developers with SDKs that allow them to take advantage of their respective smartphone operating systems or add features such as machine learning and artificial intelligence. For app developers, why reinvent the wheel?
Many app users are unaware of the fact that apps may also be sharing your user information – location and activity – with the SDK providers and others. In addition to users not knowing what information is being shared and with whom, the app developers are also sometimes unaware.
- Ad Tracking: On desktop and laptop browsers, website administrators use cookies to personalize your user experience. Cookies are also used to track your browsing activity and serve advertisements. However, on smartphones, cookies are not as effective, so companies use your device’s Mobile Advertising Identifier to serve you personalized ads. The Mobile Advertising Identifier is a unique identifier used to identify and target mobile phone users. The ID does not contain personal details about you such as your name or address; it identifies your phone and, based on your app usage, activity, or location, will send relevant advertisements to your device. One reason apps are available for free or at low cost is because they are supported by ads. If you ever wondered why you see advertisements for new cars after visiting an automobile dealership, it is because your phone and the advertisers know what you have searched.
You can disable ad tracking in both Apple and Android devices.
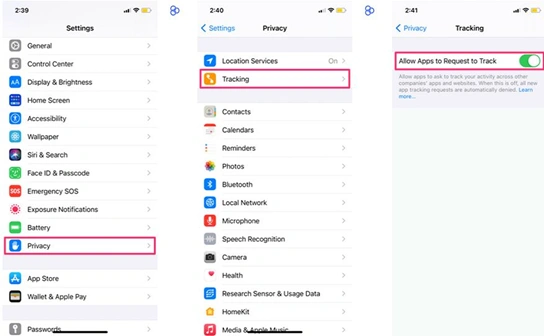
For Apple iOS devices, toggle off the “Allow Apps to Request to Track” setting under Settings -> Privacy -> Tracking. By doing so, the “Allow Apps to Request to Track” setting will be disabled for all Apple devices tied to your Apple ID. All new app tracking requests would be denied. Based on your usage and activity, you may still see some targeted ads. If you prefer to allow ad tracking, you may want to consider resetting your device’s Advertising Identifier periodically to make it more difficult for advertisers to target you. More information about limiting ad tracking on Apple devices can be found in the following articles: Apple Advertising and Privacy Reporting.
 |
 |
|
Apple Ad Tracking Settings |
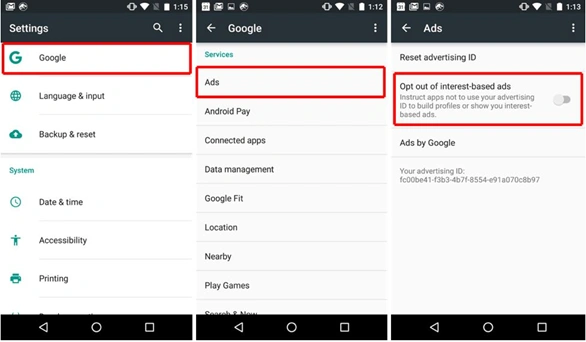
Android Ad Tracking Settings |
For Android devices, disabling ad tracking is a similar process. Toggle the “Opt out of Interest-Based Ads” setting found under Google -> Services -> Ads or Settings -> Privacy -> Advanced -> Ads. From the same screen, you can reset your device’s Advertising ID.
Some ad-tracking companies have also provided users with the ability to opt out of having their information included in their databases.
- Browser Settings: Your mobile device browser activity also provides advertisers, data brokers, and others with a treasure trove of information about you. The Apple Safari and Google Chrome browsers included with Apple and Google devices, respectively, provide users with a few settings to help manage your privacy.
To adjust the privacy and security settings in Safari, navigate to Settings -> Safari and toggle on/off the setting as appropriate.
- Prevent cross-site tracking: Toggling this setting will prevent sites from tracking where you go and what you look at when visiting other sites.
- Block all cookies: Cookies are created when you visit a site and can be helpful in personalizing your user experience, but they also may be used to collect information on you and serve advertisements. Blocking all cookies will also prevent cross-site tracking; however, it may also result in a less than acceptable user experience, especially for sites you visit frequently.
- Clear browsing history
Additional information on Safari browser privacy settings can be found here.
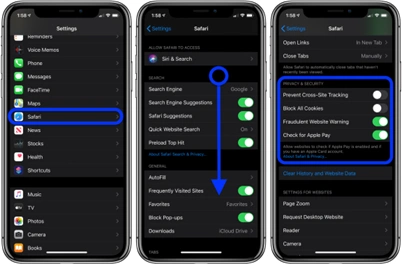 |
| Safari Settings |
On an Android device, open the Chrome browser and tap the icon containing three vertical dots and select Settings -> Privacy from the menu. Toggle the “Do Not Track” switch to prevent tracking across sites and consider clearing your browsing history. More information on Chrome’s privacy settings can be found here, and find details on safe browsing here.
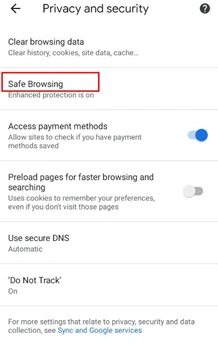 |
| Chrome Settings |
Conclusion:
Disabling location services, managing your mobile apps, limiting ad tracking, and enabling privacy settings in your device’s browser will help mitigate the risks of being tracked or having personal information exposed. However, they will not eliminate these risks. Following these recommendations may also result in diminishing the utility and functionality you expect from your smartphone. While this article has focused on many of the abuses of location tracking, there are valid reasons for organizations to collect and track users’ locations. For example, during the COVID-19 pandemic, location tracking has helped prevent the spread of the virus.
Monetizing user information through advertisements is a successful business model that has worked for companies like Google, Facebook, and many others in the internet technologies industry, but it comes with the potential for privacy abuses. With the plethora of user information collected through mobile devices, nations that do not respect user privacy, terrorist groups, and others with nefarious intentions may develop apps that seemingly provide functionality, recreation, or other user value, but instead act as a front for gathering intelligence to further their illicit activities. While you may not pay for a mobile service or application, it will often cost you in the form of your personal user data.
Further Reading:
The following selected resources provide readers with additional information on mobile device location privacy concerns and some risk mitigation strategies:
- New York Times: One Nation, Tracked - An Investigation Into the Smartphone Tracking Industry
- Vox: The Hidden Trackers in Your Phone, Explained
- Wall Street Journal: Your Location Data Is Being Sold—Often Without Your Knowledge
- Vice: I Gave a Bounty Hunter $300. Then He Located Our Phone
- National Security Agency: Limiting Location Data Exposure
- New York Times: How Mobile Phones Became a Privacy Battleground—and How to Protect Yourself
- New York Times: How to Protect Your Digital Privacy
- Computerworld: How to Stay as Private as Possible on Apple’s iPad and iPhone
- Comparitech: How to Protect Your Privacy on Smartphones and Tablets
- Digital Trends:How to Improve Your Android Privacy
- CNET: 7 Security Tips to Keep People and Apps From Stealing Your Data
- CNET: Protecting Your Privacy in the Post-Roe US
- Apple: Browse Privately in Safari on iPhone
- CDC: Mobile Privacy Policy
Featured Content
- Increase in SEO Poisoning and Malvertising>
- Sextortion and Romance Scams: Dodging Cupid’s Malicious Arrow>
- Schemes Using Deepfake Technology on the Rise>
- Uptick in Compromised Accounts>
- FBI Warns of New Tech Support Scam Targeting Senior Citizens>
- Volt Typhoon Targets Legacy Cisco Routers in New Campaign>
- Critical Infrastructure Cybersecurity Outreach Program (CICOP)>






