Credential Stuffing
Informational Report
Original Release Date: 3/31/2021
What is Credential Stuffing?
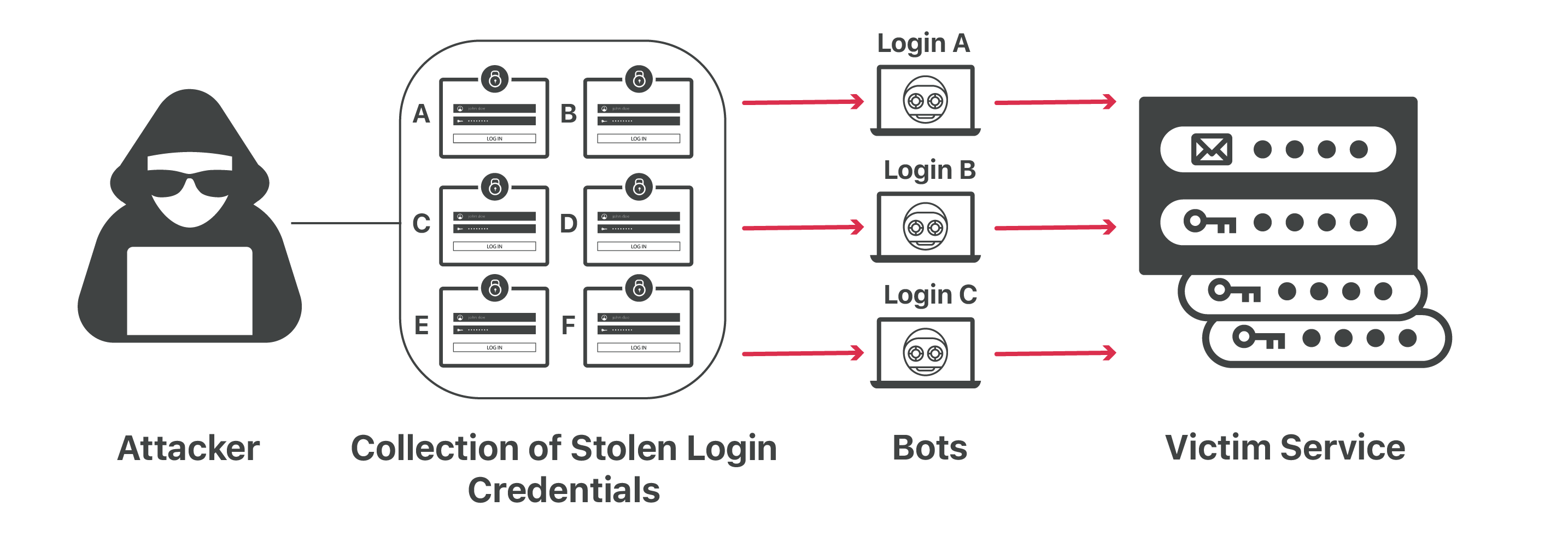
Credential stuffing is a type of cyberattack in which threat actors attempt to access online accounts using compromised user credentials exposed in a data breach. Lists of compromised credentials are often found on dark web forums or for sale on dark web marketplaces. Once these lists are obtained, threat actors can use scripts to automate the process of attempting to access online accounts using these credentials. These attempts can be successful when a user reuses a password across multiple accounts; therefore, exposed user credentials for account A can result in the compromise of account B. Account compromises can lead to identity theft, financial theft, and further cyberattacks, including network compromises and data breaches.
Image Source: Cloudflare
Recommendations
Users
While cyberattacks using credential stuffing are increasingly common, they succeed when users reuse credentials across multiple accounts and do not enable multi-factor authentication. Therefore, users are advised to use unique and complex passwords for each online account. This can be more easily accomplished with the use of a password manager; users are encouraged to thoroughly research providers prior to use. Additionally, enable multi-factor authentication (MFA) for every account that offers this feature. MFA is one of the best defenses against password-enabled account compromises. MFA is the use of two out of three possible factors - something you know, something you have, and something you are. Enabling MFA prevents account compromises resulting in password exposure or guessing, including credential stuffing attacks. While a user may use the same password across multiple accounts, the threat actor will be unable to access the targeted online account unless they have the second factor. Some methods of MFA are preferred over others; however, any method of MFA is better than none at all. The NJCCIC recommends the use of an authentication app or hardware token as a second factor over the use of SMS text or email codes.
Network Defenders
Require MFA for all users. If this is not feasible, require MFA for at least all privileged users and for access to more sensitive accounts.
Implement a CAPTCHA/reCAPTCHA. This tool can help to filter out most bots and automated scripts used to attempt access to online accounts. At a minimum, a reCAPTCHA should be required for suspicious IP addresses such as TOR nodes, proxies, and virtual private networks (VPNs).
Set login attempt limits. After a certain number of failed login attempts, it is advised to lock the account. This should include accounts with MFA enabled, where the login attempt uses the correct password but is unable to login. Additionally, login attempts could be restricted due to variations in a user's "normal" login parameters, including IP location, operating system, browser, and time zone.
Monitor login activity. Identify suspicious events, abnormal patterns, or anomalous behavior that could indicate an account has been compromised.
Use a web application firewall. Web application firewalls (WAFs) can be used to help detect and prevent attacks (such as credential stuffing), block bots, and limit the impact of an account compromise.
Monitor the dark web. Companies that specialize in monitoring the dark web can be used to gain visibility into these networks and help to identify exposed credentials before they are used to access user accounts.
Apply a geofence. Where appropriate, geofencing where users are permitted to login from can limit unauthorized login attempts.
Educate users. Ensure users maintain awareness of current cyber threats and best practices for password and account security.
Resources
SEC - Cybersecurity: Safeguarding Client Accounts against Credential Compromise
NIST - Digital Identity Guidelines
NJCCIC - Multi-Factor Authentication (MFA): A Critical Step for Account Security
FBI - Cyber Actors Conduct Credential Stuffing Attacks Against US Financial Sector