Virtual Private Networks
Informational Report
Original Release Date: 8/4/2021
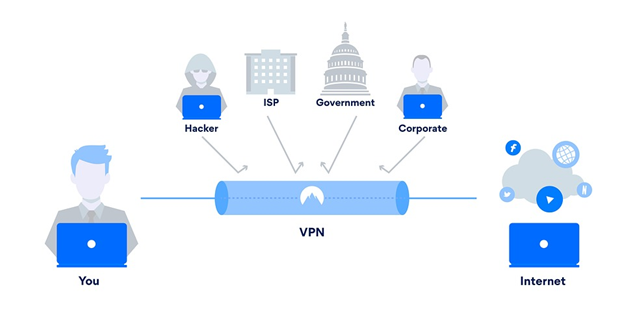
When you connect to the internet, you may be sharing more information than you realize. Typically, the effects are relatively innocuous—certain content may be restricted based on your geographical location, ads may target your preferences, and bandwidth may be throttled and lead to slowdowns. However, without protecting your device and data when connected to the internet, you may increase your vulnerability to cyberattacks and/or your online activity and consumer patterns may be sold to companies. Virtual Private Networks (VPNs) create private networks, like tunnels, across public network connections. These tunnels provide a hidden and secure means to transport information; therefore, VPNs assist in protecting data and devices from malicious and/or unwanted cyber activity.
Image Source: AT&T Cybersecurity
How VPNs Work
A domain name is a user-friendly representation of an IP address, for example Google.com for the IP address 8.8.4.4.
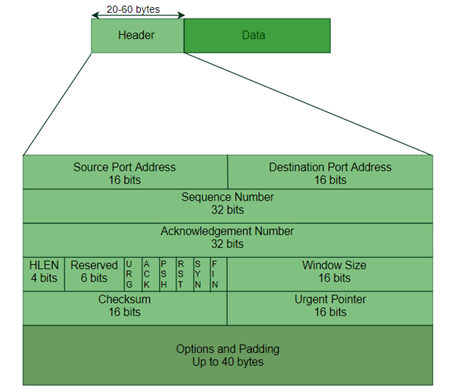
When entering a URL into a browser, for example https://www.cyber.nj.gov/ a server on the backend translates the URL to the website’s IP address. Like telephones, which have a unique phone numbers for each device, IP addresses identify devices on a network. When you type in an address such as www.cyber.nj.gov, the domain name server (DNS) converts this to an IP address, requests information from the internet through the Internet Service Provider (ISP), which routes traffic from your device out to the larger network that is the internet, and then sends the information back to your device and browser. The information is sent and received in “packets” containing headers that allow the network to understand where to send the information.
Image Source: GeeksforGeeks
These packets contain the destination (such as www.cyber.nj.gov) and the source (your device's) IP addresses, as well as data to send and receive, such as login credentials or other sensitive information.
During these requests, information about the device – such IP address – may be intercepted when sent through a network, especially when connected to an unsecured public Wi-Fi network.
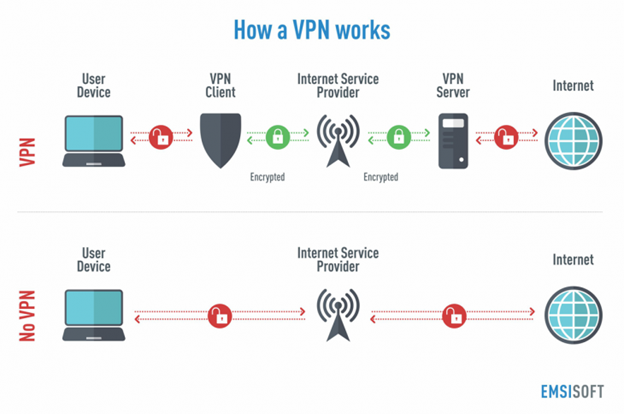
To protect data from being intercepted and used in subsequent attacks, VPNs establish secure connections by encrypting data and using virtual IP addresses so that the user’s digital footprint and browsing activity cannot be accessed by ISPs or nefarious threat actors. These virtual IP addresses conceal a device’s true location. Many VPNs also offer the option to reroute traffic via another country in order to access content only available in foreign countries, and is often used to avoid strict government-imposed internet censorship.
Image Source: Sucuri
The use of VPNs is highly advised for when connected to unsecured or public networks. Although it may not be necessary on home Wi-Fi networks, the ISP does have access to the user’s information and may be permitted to sell the data. Using a VPN as a general cybersecurity best practice ensures that data is encrypted and secure from IPSs and various third parties.
VPN Use
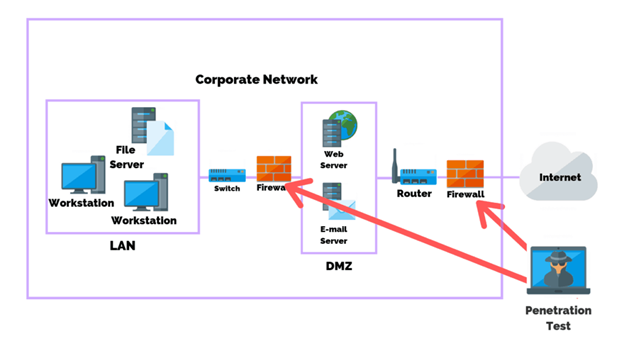
VPNs were originally commonplace in only professional settings, such as enterprises, organizations, or governments, to secure data while employees worked online remotely. Due to the COVID-19 pandemic, there has been a surge in VPN usage as more employees than ever before began working from home. Corporate and government networks often contain sensitive data, such as personal employee information, intellectual property, trade secrets, or classified information. Organizations most likely use firewalls and other security appliances to protect this sensitive information.
Image Source: PurpleSec
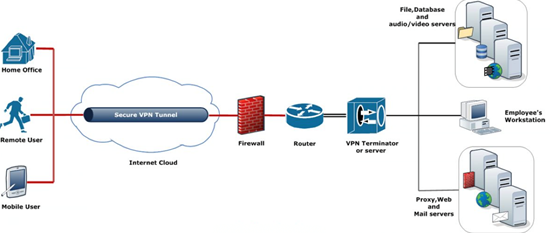
An intranet, a private physical network of devices that prevents access to the resources from outside the network, typically is protected by a firewall. Remote employees may require access outside of the intranet’s perimeter without compromising security. Therefore, organizations may have employees connect to a VPN to provide a private, encrypted virtual link as if the device has a direct physical connection to the network.
Image Source: Finchloom
VPNs are not just for business purposes. Individuals are advised to use VPNs for personal use when connecting to available public Wi-Fi networks because information could be intercepted and used for nefarious purposes. For example, an individual may connect to a coffee shop’s public network to check their bank statement. When logging into the bank’s website, the IP address, account credentials, and other sensitive information are sent and could be intercepted without the use of VPN.
While VPNs provide security benefits, they may also be used for malicious purposes. When a threat actor uses a VPN, their location and information is obscured and, therefore, can be challenging and difficult to trace. Network defenders often consider blocking network traffic from countries that are notorious for engaging in cybercrime; however, threat actors from these countries could simply use a VPN to evade location-based restrictions as well as hide their tracks, as VPNs obscure use data.
Considerations for VPN Usage:
There are free and paid options for VPNs. One concern when using a free VPN is that these services often collect, store, and sell user information in order to make revenue, commonly leading to targeted ads. In addition, data may not be sufficiently secured and could be compromised. It is also important to verify that certain permissions or functions are removed to prevent third-party access. Some free providers may not have the means to thoroughly verify and validate software code, which could lead to user issues or vulnerabilities and put devices at risk. Another important consideration is the speed of internet access. Many free VPNs share bandwidth between users. The service may aggregate the bandwidth and increase profits by selling it to a bidder, who may use it for nefarious purposes.
Oftentimes, the paid VPN services provide higher quality and security for its users. Be sure the services are compatible with the system requirements, including operating system such as iOS, Windows, or Linux. When purchasing a VPN, make sure to check that the service keeps data secure by using a strong, standard encryption scheme; many VPN services advertise using military-grade encryption standards. Also, verify the provider has many server networks and locations. Finally, consider a provider with a zero-logging policy, which ensures that no user data is stored by the service, including records of personal information, traffic, and downloads in order to provide strong data and privacy protections.