Passwords, Passwords, Passwords
Garden State Cyber Threat Highlight
Original Release Date: 5/4/2023
Original Release Date: 5/6/2021
Updated May 4, 2023
The first Thursday in May is World Password Day, which was originally created by Intel in 2013 as a global effort to address the critical need for strong, unique passwords and emphasize the importance of this first line of defense. This day also serves as a reminder to update and organize all recent passwords. Users access hundreds of personal accounts ranging from email and social media to online banking and bill pay, healthcare, entertainment apps, Internet of Things (IoT) devices, and more. Likewise, employees must maintain multiple accounts and services, including email, applications, and vendor websites. The increased use of online accounts and services, combined with users engaging in risky password management practices, puts both themselves and employers at risk of account compromise and data breaches. Therefore, it is important to practice good password hygiene to protect accounts and data year-round.
What is a Password?
According to the National Institute of Standards and Technology (NIST), a password is a secret that a claimant memorizes and uses to authenticate his or her identity. Passwords are typically character strings and can include letters, digits, or other symbols. Passwords can also be numeric only and are referred to as personal identification numbers (PINs). In addition, passwords can consist of words and other text to create passphrases, which are easier to remember and generally longer.
Creating and Managing Strong Passwords
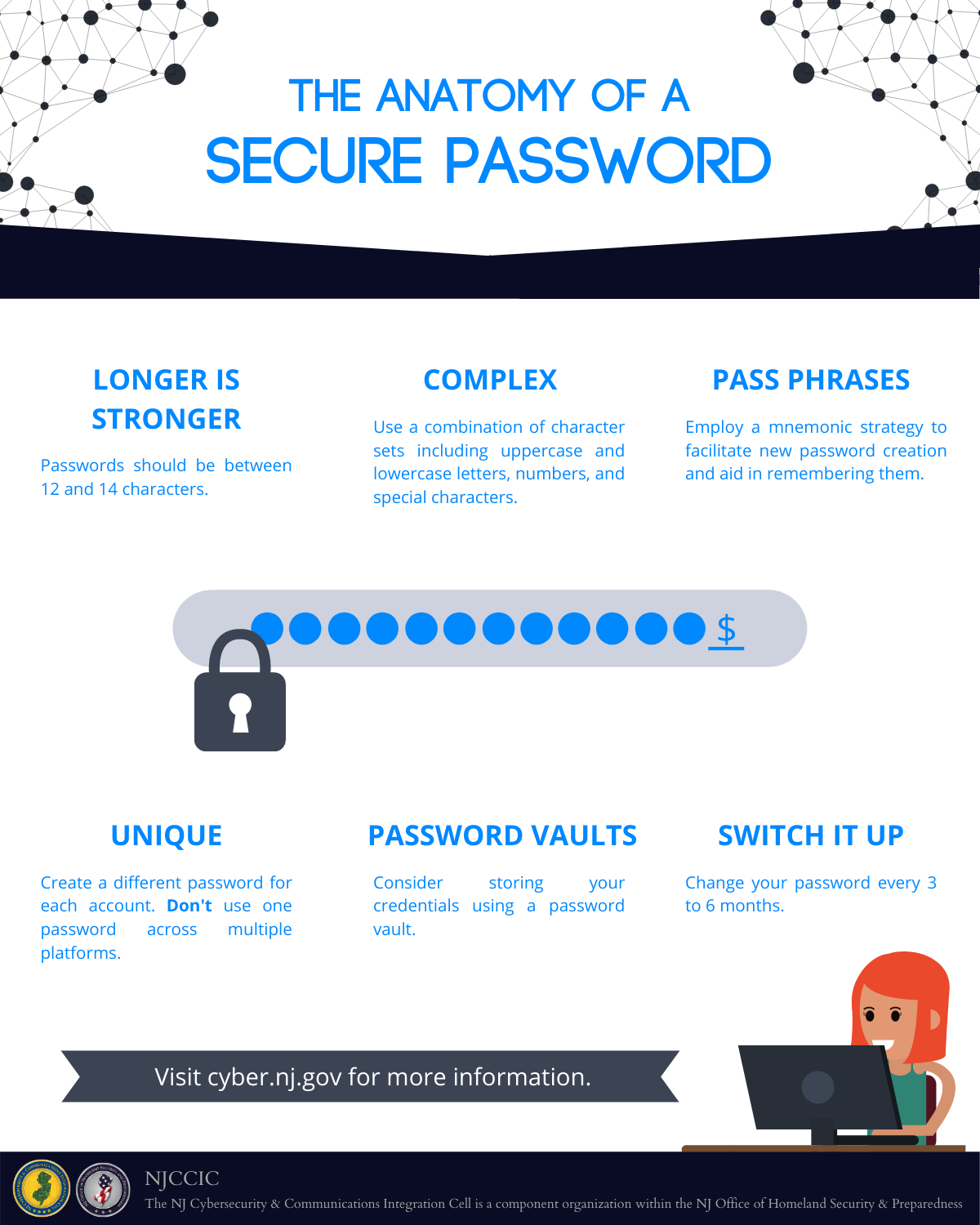
Most organizations specify a password policy, which will include requirements for password composition and usage. Both length and complexity are important when creating a password. Each additional character exponentially increases the possible combinations a hacker’s tool needs to compute in order to identify the targeted password. Additionally, the letters used within the password should not create a word that can be found in the dictionary as these hacking tools ingest the millions of user passwords exposed in data breaches, which creates libraries of the most common dictionary words, numbers, and symbols used in passwords. The elements of personal information should also be avoided when creating both passwords and password hints because they can be easily accessed or guessed, particularly after combing through social media accounts. This information may include names of people or pets, anniversary dates and birthdays, phone numbers, sports teams, and favorite holidays.
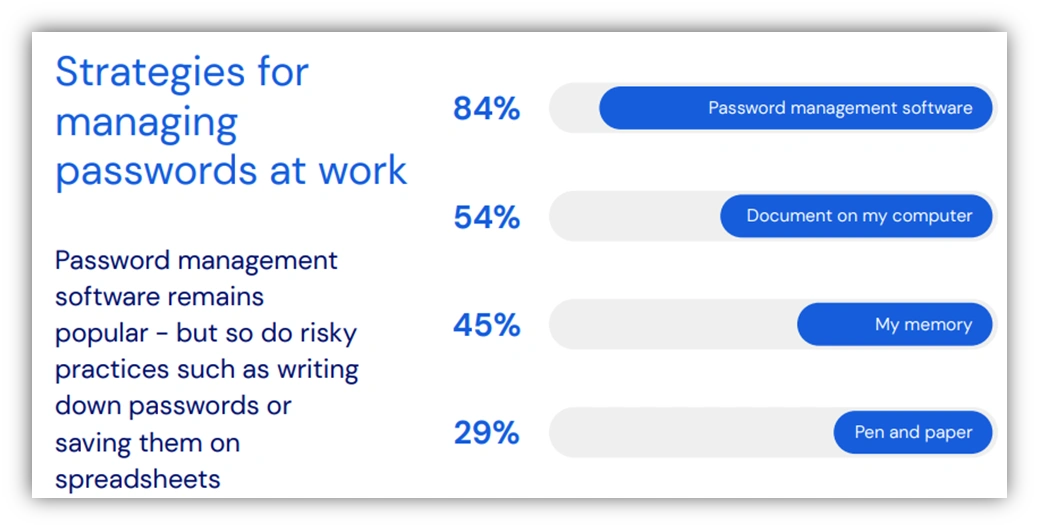
According to a recent survey, the average user has around 100 passwords and suffers from password overload, which can make retention difficult and impractical, and often results in password reuse. Another survey found that users manage their passwords by memory (45 percent), pen and paper (29 percent), documents on computer (54 percent), and password management software (84 percent).
Image Source: Bitwarden
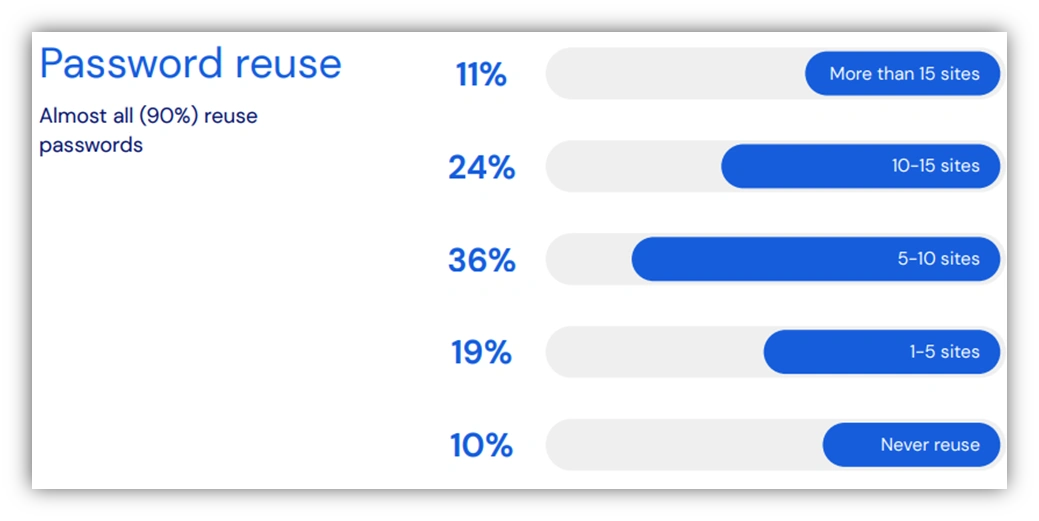
This survey indicates that users continue to rely on memory and, consequently, tend to use weak passwords that are easy to recall, which also means they are easier to guess or crack. When the time comes to change or create new passwords, users often reuse the same password, and simply add one new letter, digit, or symbol at the end. These common pitfalls of using and reusing weak passwords across multiple accounts make it easy for threat actors to compromise several accounts using the same credential. Threat actors have various hacking tools to crack passwords and conduct brute force attacks. These malicious tools use algorithms to repeatedly guess passwords until the correct combination is found. It is not if a weak password can be cracked, it is a matter of how much time and resources it will take to determine the correct combination. The consequences of weak password reuse can also extend to other cyberattacks, data breaches, financial loss, loss of business continuity, and regulatory compliance violations.
Image Source: Bitwarden
Password overload and retention also impacts organizational productivity and security as users may give up and ask their help desk to reset their passwords, which ties up organizational resources. Users may also scramble to find passwords stored in unencrypted spreadsheets on connected devices, written down on sticky notes or paper, stored in browsers, and other insecure methods. Password management applications are one solution to password overload and retention. These applications can fulfill password requirements by creating strong, unique passwords that are difficult to guess or crack, remembering passwords, and storing passwords safely using a master password and strong encryption. Password management applications offer additional features and plans, so choosing a password manager depends upon the needs of the organization or individual. Although these applications can be attractive targets in which threat actors attempt to compromise the master password and gain access to many credentials, the benefits of these applications outweigh the risks.
Data Breaches
Account credentials are often stored without encryption. Strong, unique passwords are not a standalone security solution. If a password is stolen in a data breach and sold on the Dark Web, the strength will not matter. Reusing passwords for multiple accounts invites the potential for password compromise, unauthorized account access, cyberattacks, and data breaches. The more a password is used, the more likely an account will be compromised. For example, if users use their work password for personal accounts, a data breach can put organizations at significant risk by potentially giving threat actors the ability to further compromise vulnerable people, accounts, systems, and networks in order to access and exfiltrate data.
Multi-Factor Authentication (MFA)
The practice of password reuse, combined with an increase in cyberattacks, data breaches, and Dark Web and public disclosures, necessitates the adoption and implementation of additional account security requirements, such as multi-factor authentication (MFA). Account compromises resulting from password theft, disclosure, or guessing can largely be prevented by enabling MFA, where available. Authentication factors included in MFA are something you know – such as a password or PIN, something you have – such as a badge or one-time code, and something you are – such as biometrics. MFA is an effective measure to protect users from account compromise via credential theft or exposure. Even if a threat actor gains access to an account password, they will not be able to access the associated account without the user’s additional factor of authentication.
Recommendations
The many steps to improve password hygiene include strong and unique passwords, password management applications, and MFA. Organizations and users can use the below graphic provided by Hive Systems to determine the relative strength of a hashed password against a cracking attempt and areas for improvement.
The NJCCIC recommends users apply cybersecurity best practices to protect their accounts and data in order to reduce the likelihood and impact of attack.
- Security awareness training: Participate in training to help better understand cyber threats and provide a strong line of defense.
- Use unique, complex passwords for all accounts. Unique passwords for each account prevent password reuse attacks, in which threat actors obtain your password for one account and use it to compromise an additional account using the same credentials.
- Refrain from sharing or saving login credentials or other sensitive information. Login credentials and other sensitive information should not be shared with anyone or posted in plain view. Avoid auto-saving passwords, payment card numbers, or contact information when prompted by your operating system, web browser, website, or applications.
- Enable multi-factor authentication (MFA) where available. MFA is the use of two or more factors to authenticate to an account or service. This significantly reduces the risk of account compromise via credential theft in which your password has been exposed. Even if a threat actor obtains a user’s username and password, they will be unable to access that user’s account without their second factor. The NJCCIC encourages users to choose authentication apps, hardware tokens, or biometrics as a second factor over SMS-based authentication due to the risk of SIM-swapping, though using any form of MFA is beneficial. The website TwoFactorAuth.org maintains a comprehensive list of websites that offer MFA.
- Update passwords immediately following a data breach or potential compromise. Use a resource, such as haveibeenpwned.com, to determine if your information, such as an account password, has been revealed in a public data breach. Change exposed passwords for every account that uses it to protect against account compromise.
- Exercise caution with communications. Refrain from divulging sensitive information via phone, text messaging, or email without verifying the requestor via a separate means of communication before taking any action.
- Navigate directly to websites. Navigate directly to authentic or official websites by typing the legitimate URL into the browser instead of clicking on links in messages, and refrain from entering login credentials on websites visited via links delivered in messages.
- Use secure websites. When sharing personal or financial information, ensure you are using verified, secure, and encrypted websites.
- Change default passwords. Default passwords for accounts/devices can be used to gain unauthorized access.
- Secure physical devices. Safeguard devices and ensure a password/passcode is enabled for all devices to prevent unauthorized access.
- Keep devices up to date. Stay informed about publicly-disclosed vulnerabilities and update devices—including firmware—to the latest version to ensure they are patched against known vulnerabilities that could be exploited by threat actors to gain unauthorized access to your device and/or data. If a device is unable to receive updates from the vendor, consider not purchasing or discontinuing use of the device.
- Report incidents: Report malicious cyber activity to the NJCCIC via the Cyber Incident Report form.